Have you heard of Air-Gapped computers? If not, then let me tell you that those computers that aren’t connected to the internet, Wi-Fi, and even Bluetooth are called air-gapped computers. Mostly in industrial environments, these kinds of computer systems are used to protect the machinery or production system from unwanted access, and also often it’s used to protect the sensitive data of the industry. Whatever the reason for using air-gapped computers, no one can tell that even air-gapped computers can’t be exploited. There are so many techniques to exfiltrate the sensitive data of an air-gapped computer but the recent technique with the name Covid Bit is much more dangerous.

What is Covid Bit?
The name “COVID-bit” – is kinda confusing, since it doesn’t have anything to do with covid. With the help of the technique ‘Covid bit’, one can easily exfiltrate files from air-gapped computers by exploiting a computer’s power supply. A hacker can remotely receive files using their smartphone from up to 2 meters away – without using WiFi, Bluetooth, or the internet.
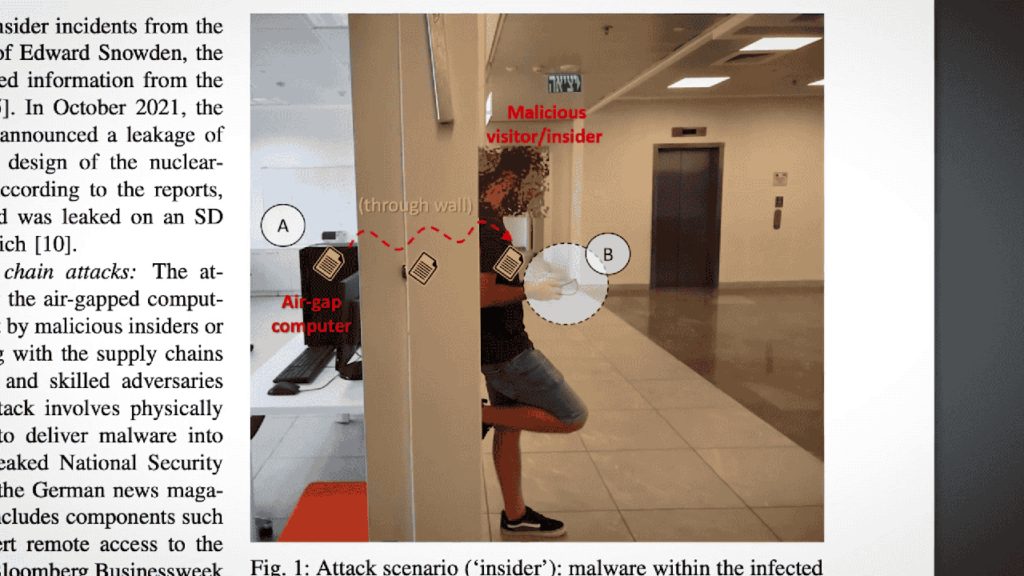
Now you may think is it really possible to exploit a power supply? Well technically, no because the power supply has no such hardware implemented which can copy or duplicate files or user-input keystrokes from the PC. The power supply’s job is to deliver the required power of the system but there’s something that can be tracked.
How Data Can be theft using Power Supply?
First of all, you have to understand how the power supply works. The power supply in our computers is generally a kind of Switch Mode Power Supply. The name clarifies that it has some sort of switching frequency. I am not going into much detail but the point is the power supply’s output voltage and current is controlled by switching the input voltage on and off at very high frequencies. The rate of switching depends on how much power the computer is consuming.

While doing the job, the power supply because of this switching emanates small amounts of electromagnetic radiation. It is also mentionable that if a computer has a heavy workload assigned then the CPU needs more power to process those tasks. This excess power gradually is delivered by the power supply which affects the switching frequency thus the electromagnetic radiation.
Don’t Miss: UPS – How it Could Protect Your Computer from Power Outage?
So, if somehow the switching frequency is forcefully manipulated by regulating and controlling the workload of the CPU then by just simply picking the radiated electromagnetic radiation we can pick any file from the air-gapped computer. That’s actually done with the technique ‘Covid-bit’.
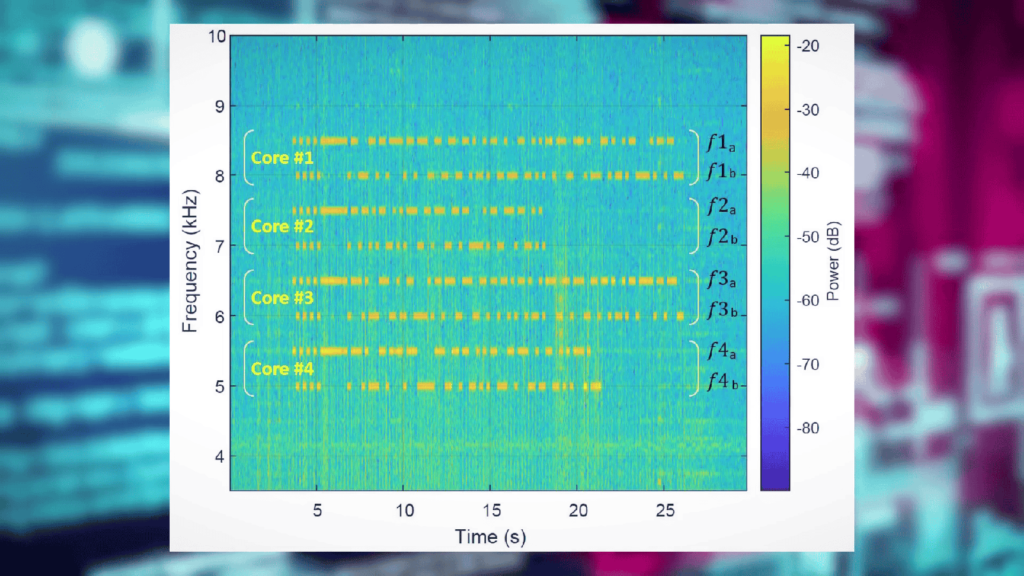
How Covid bit Works?
Malware on a victim’s PC would take a file, and run it through an algorithm, encoding it into a CPU workload which would then be run on the processor. The power supply would be forced to account for the variations in power consumption by modulating the rate of switching, which would create a stream of electromagnetic radiation.

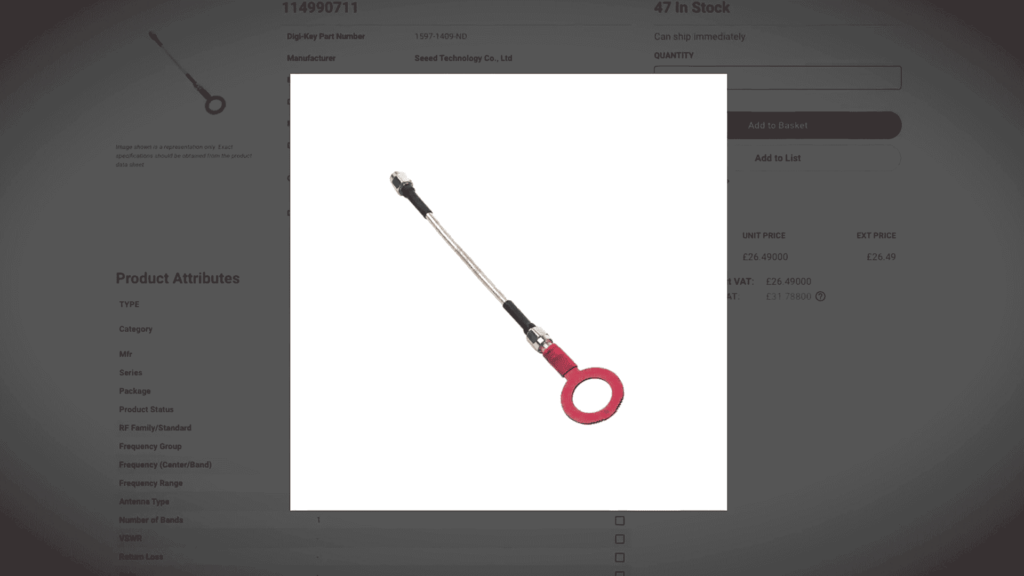
This electromagnetic radiation can easily be picked up by a smartphone. A small loop antenna as shown in the picture below is connected to the phone’s 3.5mm audio jack.
The power supply generates radio signals in the low-frequency bands between 0 to 60 kHz which is a workable range of the audio hardware of the smartphone so it can easily be decoded with the right algorithm.

There’s a demonstration video, that shows a string of text transmitted to a phone behind a wall – so this does work.
One of the great advantages of this exfiltration method is that it doesn’t need admin privileges, so the computer never understands or blocks this malware to do its job and even it can run in a VM, which is a big bonus.
Greatest Disadvantages of Covid bit
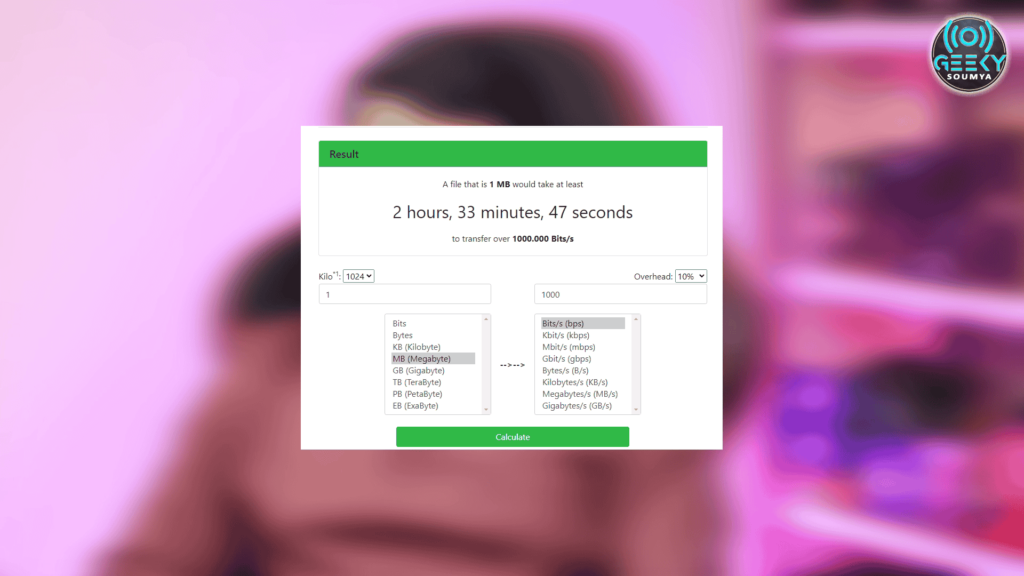
Until now you know the advantages which Covid bit offers but if we count the disadvantages it’s quite a few. One of the most significant disadvantages is the transfer speed. Maximum this technique reaches up to 1000 bits per second. So, to transmit a megabyte you have to wait for 2 hours – quite impractical of using this in the real world.
Another disadvantage is the transmission range. You have to stay within 2 meters radius of the victim’s PC and since the communication is only one-way, the time and date of the exfiltration would have to be pre-determined in malware. The hacker can’t control anything. Also here we are assuming all of this is done in room housing. In case the air-gapped computer is in a faraday cage there’s no transmission is possible. Of course, delivering the attack to an air-gapped computer isn’t easy. Only a spy or rogue employee could install the malware on a victim’s PC using a USB drive or something similar.
Also Read: How to Add Extra USB, HDMI, and Ethernet ports On laptop?
What Can be Stolen by using Covid Bit?
As I mentioned earlier, the transfer speed of this technique is too slow to transfer anything useful but small documents, passwords, and keystrokes can easily be transmitted.
Aren’t We Safe Anymore?
Definitely, Covid Bit is a dangerous technique but because of a lot of limitations, this technique is probably never going to see the light of day. The researcher behind it, is “Dr. Mordechai Guri” is actually quite famous for coming up with different ways to exfiltrate data from air-gapped computers, whether it’s repurposing a SATA cable to act as an antenna or encoding data in sound waves emitted in the resonance frequencies of a phone’s gyroscope, etc. Hope you guys have enjoyed this article and learned about the possibilities of snitching data from computers. If you really think this article is worthy of your time then share it with your friends and comment down below to appreciate our work. Thanks for visiting.
